Recently I pointed out in a blog post that the Zoom CEO was the VP of Engineering at Cisco who left to start a direct competitor because, according to him, he was unhappy about the speed he could operate at.
Being secure, to be frank, is about flaw management practices such as transparency and handling much more than being devoid of flaws. How one educates users about a serious bug should be in the spotlight right now and Zoom is failing catastrophically.
Reading between the lines it looks a bit like the CEO didn’t like being told to do the right thing (follow safety processes) by Cisco management, and he allegedly saw it as an opportunity to exit and do a much easier thing — get rich doing what’s wrong, then apologize and hope for no accountability.
So let’s put this business management theory to a simple product security management test.
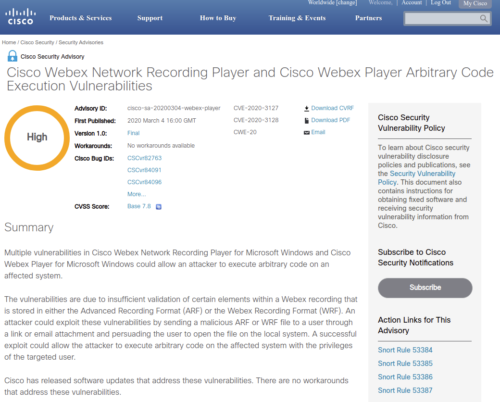
Here is a 2020 WebEx security vulnerability advisory:
I’d rate that security page and overall site as excellent and extremely useful to keeping everyone safe.
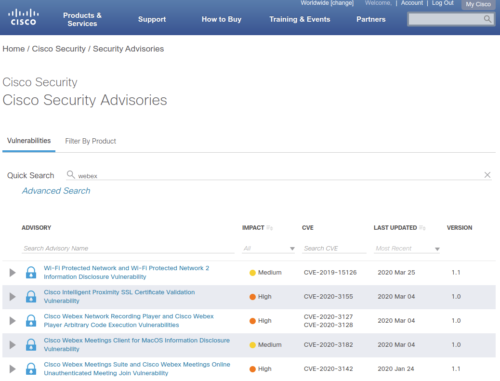
It stems from the main cisco.com/security page, where you can easily query and sort on WebEx vulnerabilities.
Let’s now compare that level of transparency and operational excellence to the Zoom outfit, run by the celebrated billionaire CEO.
First, the zoom.com/security page is a lot of marketing material fluff. We know already that these marketing materials are deceptive (e.g. end-to-end encryption is claimed, yet in reality it’s client server using a shared key that’s half the strength claimed and distributed in China…but I digress).
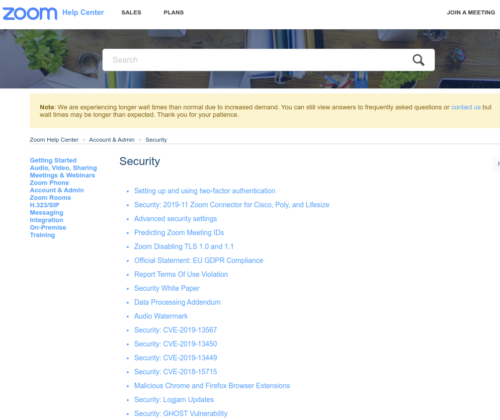
You have to scroll all the way to the bottom (it’s long) to find anything about security practices, like patches and advisories. Even then, security practices appear at first glance to be severely lacking, hosted at this oddly complicated US support URL.
https://support.zoom.us/hc/en-us/sections/201728933-Security
Second, I will test this support page using Patrick Wardle’s announcement (“The ‘S’ in Zoom, Stands for Security: uncovering [local] security flaws in Zoom’s latest macOS client“) from March 30, 2020.
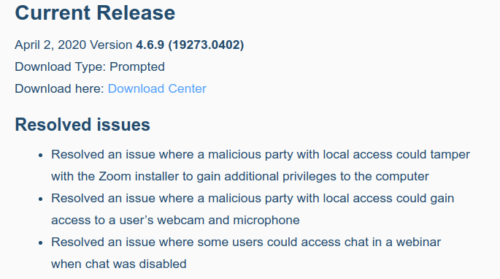
Patrick kindly has updated his own announcement page in April that “Zoom has patched both bugs in Version 4.6.9 (19273.0402)”. Was the Zoom response well done? No.
Look very closely and very carefully at the Zoom security practices page:
A huge security news story, details about the vulnerability, announcement of the patch… none of it, nothing at all can be found anywhere in this support page or the top-level security page.
How would you know to update for a security flaw or even who it affects and how bad it is when it doesn’t appear anywhere except an obscure security researcher’s personal blog page?
I’d rate that as awful, and way below industry practices (again, look above at WebEx). This company supposedly obsessed with technology being “easy and fast to use” has a terribly convoluted hidden security site with CVE tossed in like a mixed bag among some random thoughts by their support team that hasn’t been updated in half a year.
It’s April 2020 and given the news so far this year there should be far more CVE on this page (even if only placeholders, we’ve seen one for Windows and one for OSX).
That’s just to begin with, as this really should elevate to a zoom.com/security URL and be easily sorted and searched as well as linked to product release/fix notes. I would imagine a truly sorry CEO would put up a giant box on the top level security page that says the industry standard WARNING: SECURITY FLAW.
Do it now Zoom, if you really are interested in moving fast.
Third, pop over to the release notes for the version Patrick mentions, which aren’t even linked from this page, you won’t find the word security mentioned anywhere.
This is unbelievable levels of bad management practice. Both the security page and the release page are far below acceptable. The practices are truly below baseline and should fail regulations and audits.
Please, anyone, someone explain to me why these release notes don’t use the word security anywhere, let alone don’t have a CVE with details and aren’t connected to the security advisory page.
There’s really not a need at this point for me to get into interesting and messy details of CVE, CWE, CVSS, etc when it’s obvious just how far below a safe baseline Zoom is operating.
I’ve shown enough already how Zoom practices may be a danger to society.
My take on this is the CEO has not enabled his security team (buried in US support), is not listening to his security critics (2020 vulnerabilities not listed), and does not yet take security seriously (sends out apologies to get sympathy without making necessary changes).
I may be forced to look further.
It’s like watching a dumpster burning and hard for me to take my eyes off at this point. Ok, ok let’s go just a little bit onward.
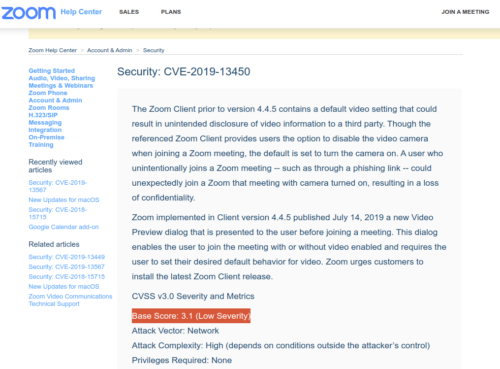
Fourth, I drop down into Security: CVE-2019-13450 shows Zoom has a severity score of 3.1 out of 10 (CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:L/I:N/A:N):
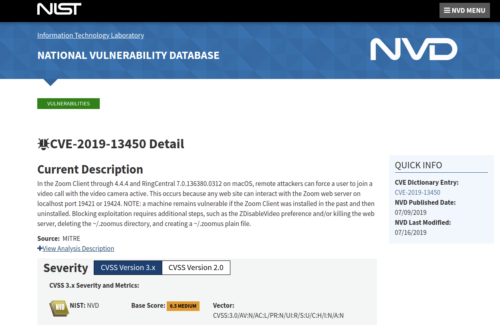
HOLD ON TO YOUR HATS everyone because… wait for it… NIST shows this vulnerability officially filed as 6.5 out of 10 (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N), more than double what Zoom wrote on their security support pages!
Here are the calculations side-by-side, which shows how Zoom ended up publishing a false score in their useless security page (Attack Complexity High, Confidentiality Low) while everyone in the world will pull an official higher risk number from NIST’s database:
Zoom: CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:L/I:N/A:N
NIST: CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N
Look, I’ve spent a lot, and I mean a lot, of time inside the sausage factories called software development working on CVSS scores like these. There can be endless debates and fights and it isn’t always easy. I get that, trust me. I even established one of the first 70 CVE Numbering Authority (CNA) in the world for a major software vendor to pump out vulnerabilities that had been obscured.
But I will tell you right now that Zoom claiming complexity is high and confidentiality is low is completely and utterly wrong. It’s deceptive and it’s harmful. Here is the excellent NIST text explaining a CVSS score of 6.5:
…attackers can force a user to join a video call with the video camera active. This occurs because any web site can interact with the Zoom web server on localhost port 19421 or 19424. NOTE: a machine remains vulnerable if the Zoom Client was installed in the past and then uninstalled…
That is a text book case of high confidentiality loss. Does it really get any higher than to be spied on from your camera? And it has a reliable service (text book case of low complexity) that remains vulnerable even after a user tries to remove it? Come on Zoom people.
From there I drop into another CVE they have listed and another, and see problems everywhere…
Their last update on vulnerabilities is from six months ago called “Security: 2019-11 Zoom Connector for Cisco, Poly, and Lifesize” which has a CVSS of 8.1 and no CVE number assigned. I get that they might not be a CNA, or have trouble getting a CVE, but it doesn’t say anything at all.
In the meantime, with no CVE and no advisories page and no links from the main security pages, who exactly is expected to know they need to patch a CVSS 8.1 from October 2019?
There are a million more examples I could give but honestly it’s just so bad I think people need to understand that a major product security and safety overhaul is overdue at Zoom.
I’m not saying anyone should use WebEx, but at least take a look at what they’re doing right to understand just how far off the mark Zoom is. I do not see anything approaching a safe product with proper management practices at Zoom.
And I don’t know if any of this yet means the CEO has to go, or that the AG and FTC should be breathing fire.
However, I can tell you as a long-time product security leader that so far everything I’m looking at from my perspective shows very broken software lifecycle; it’s substantial evidence of misleading and deceptive practices, which clearly harm customers.
Only YOU can prevent video conferencing fires.